Contents
Objective
This article is going to introduce how to configure Microsoft Entra/Azure management platform and the SAML SSO settings in Controller to achieve redirection from Microsoft Enterprise Application to Omada Controller.
Requirements
- Omada Controller (Software Controller / Hardware Controller / Cloud-Based Controller)
- Microsoft Entra/Microsoft Azure
Introduction
SAML SSO is an XML-based open standard for exchanging authentication and authorization data between parties, specifically between an identity provider (IdP) and a service provider (SP). It enables users to log in once and access multiple systems without needing to log in again at each one.
This article explains how to configure SAML SSO, using Microsoft Entra and the Omada Cloud-Based Controller v5.15.16 as an example.
Configuration
Our Configuration includes IDP Configuration,
Step 1. Go to Microsoft Entra Admin Center: Default Category - Microsoft Entra admin center. Click Applications, then choose Enterprise Applications.

Click New application to browse Microsoft Entra Gallery.

Click Create your application. Enter the name of your application and click Create.

Choose 2. Set up a single sign-on.

Step 2. Click unit SAML to start configuring the SAML Certificate.

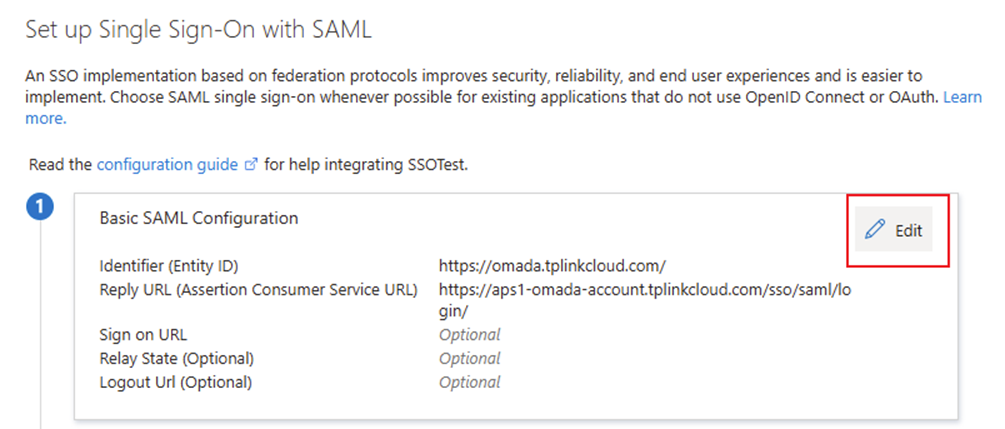
In Basic SAML Configuration, choose Edit to configure the configuration.

Here we take a Cloud-Based Controller as an example:

- Identifier (Entity ID): Here, we input the Omada Cloud’s domain into this text bar: https://omada.tplinkcloud.com/.For Software Controller& Hardware Controller, you can set the Entity ID as the “IP Address + port” of your Controller. For example, https://192.168.10.11:8043.
- Reply URL (Assertion Consumer Service URL): Here, we input the SSO login domain into this text bar: https://aps1-omada-account.tplinkcloud.com/sso/saml/login/ For Software Controller& Hardware Controller, you can set the Entity ID as the “IP Address + port + /sso/saml/login.”For example https://192.168.10.11:8043/sso/saml/login
.
Go to SAML Certificate, then click Federation Metadata XML > Download to download the IdP metadata file.

Step 3. Go to the Controller to configure the SP system. Go to Global View > Settings > SAML SSO, then click Add New SAML Connection.

In the Add New SAML Connection window, input the Identity Provider Name, upload the Metadata.xml file you just downloaded into this window, and click Send.

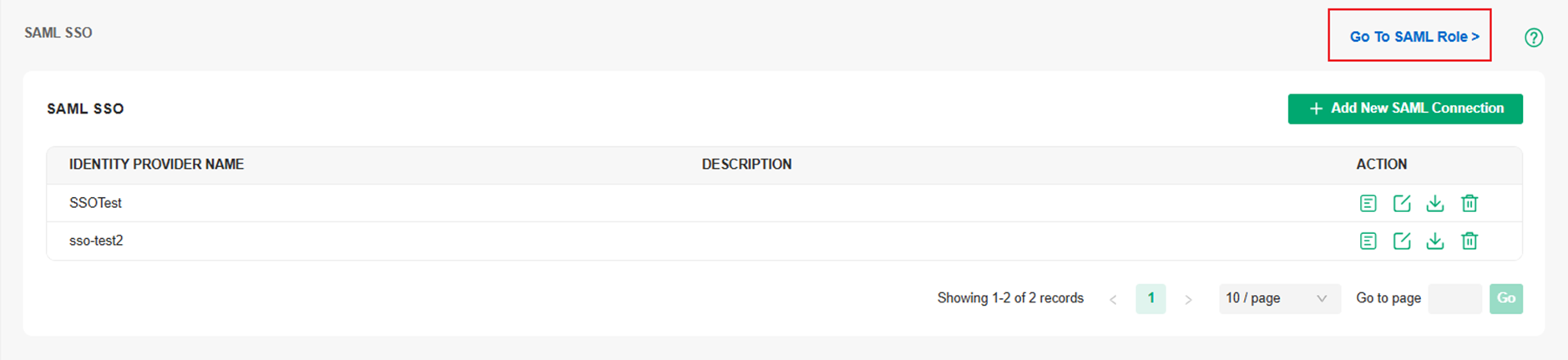
Go back to the SAML SSO Manager Page and check the Details of the entry we just configured.
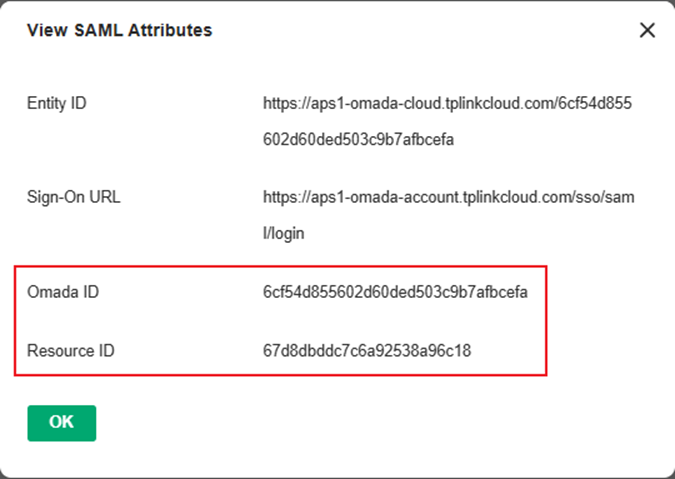
Record the information in this window, especially the Resource ID and the Omada ID.

Click Go To SAML Roles.
Click Add New SAML Role to start a new SAML role.

Set the SAML Role Name and the role’s privilege, then click Create. The name will set the SAML role on Azure/Entra.

Step 5. On Entra's homepage, click App registrations. Click the IdP you created.
In Basic SAML Configuration, choose Edit to configure the configuration.

- Identifier (Entity ID): Input the Entity ID we obtained from the Controller’s SSO Detail.

- Reply URL (Assertion Consumer Service URL): Input the Sign-On URL we obtained from the Controller’s SAML Attributes.

- Sign On URL(Optional): This text bar should be blank. Please don’t confuse this with the Sign-On URL we obtained from the Controller’s SSO Detail.
- For Relay State, you must decode the script “resourceId_omadaId” using Base64. You can use any open-source Base64 encryption tool to encrypt this script.

Click App roles and create roles.

The Display name and Value here must correspond to the SAML SSO Role Name in the Controller.

Step 6. On Entra's homepage, click Enterprise Applications. Click your application, then click Users and Groups. Choose an account and assign a role you created

Choose to assign one role to the selected user.

Here, we take the Role “SSOtest” we created as an example and assign it to our selected user.

Step 7. On Entra's homepage, click Enterprise Applications. Click your application, then click Set up single sign-on.

Click the Edit in Part 2— Attributes & Claims to edit the attributes.

Click Add new claim.

Add the username as parameter. Set Name as username and the Source Attribute as the user.displayname.

Add the usergroup_name as parameter. Set Name as usergroup_name and the Source Attribute as user.assignedroles.

Download Federal Metadata XML.

Step 9. Go back to the SAML SSO unit of your Cloud-Based Controller. Edit the SSO configuration, upload the Metadata.xml file you downloaded to this window, and click Send.

Verification
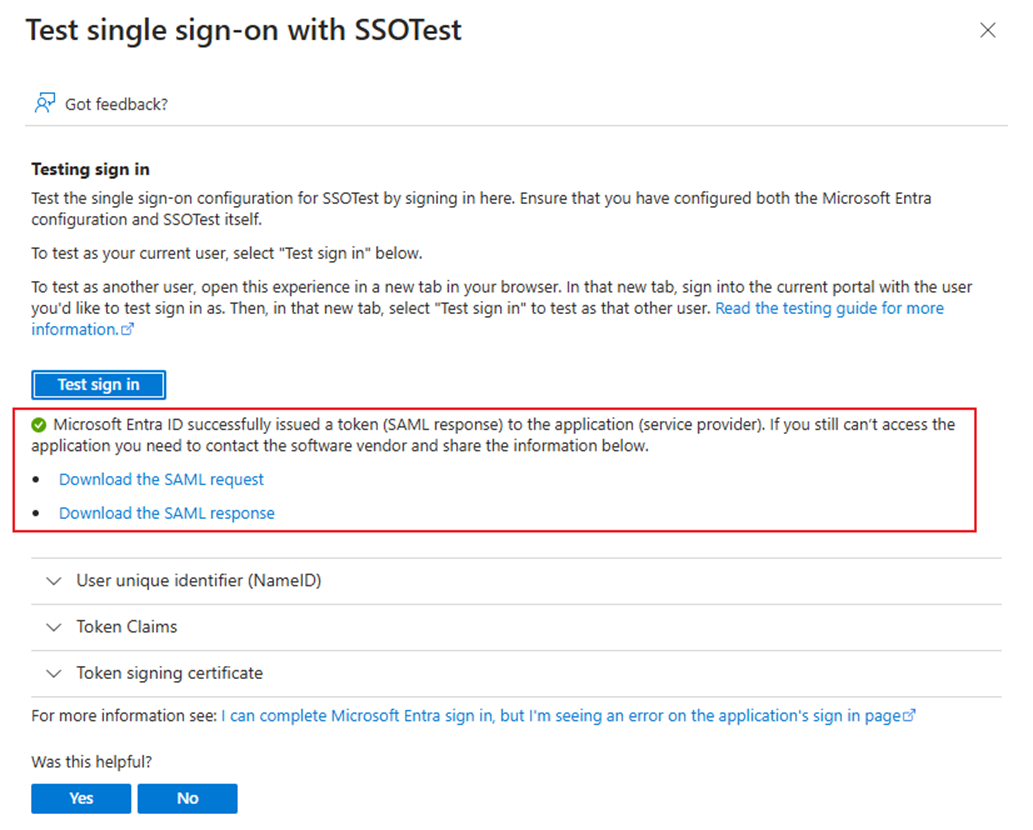
Method 1: Go to Part No.5 of your SAML-based Sign-on settings and click the Test button to test this SAML SSO.

Click Test sign-in to test whether this can redirect you to Omada Controller.

The browser will redirect you to Microsoft Login, which asks you to choose a Microsoft ID to log in. Here, we choose the user we assigned roles to in Step 6.

If the login is successful, you will return to the test page, and the test result will be shown under the Test sign-in button.
Method 2: Go to https://myapplications.microsoft.com. After logging in with your Microsoft ID, click the Application you just configured to log in to Omada Controller.

The browser will redirect you to Microsoft Login, which asks you to choose a Microsoft ID to log in. Here, we choose the user we assigned roles to in Step 6.

After logging in, you will be redirected to your Omada Controller.
Conclusion
You have successfully configured the SAML SSO of Omada Controller with Microsoft Entra/Azure ID.
Get to know more details of each function and configuration please go to Download Center to download the manual of your product.
FAQ
1. What should I do if the browser reports a While Label Error Page? After checking the dev tools windows, there’s also the error code “405 Method Not Allowed.”
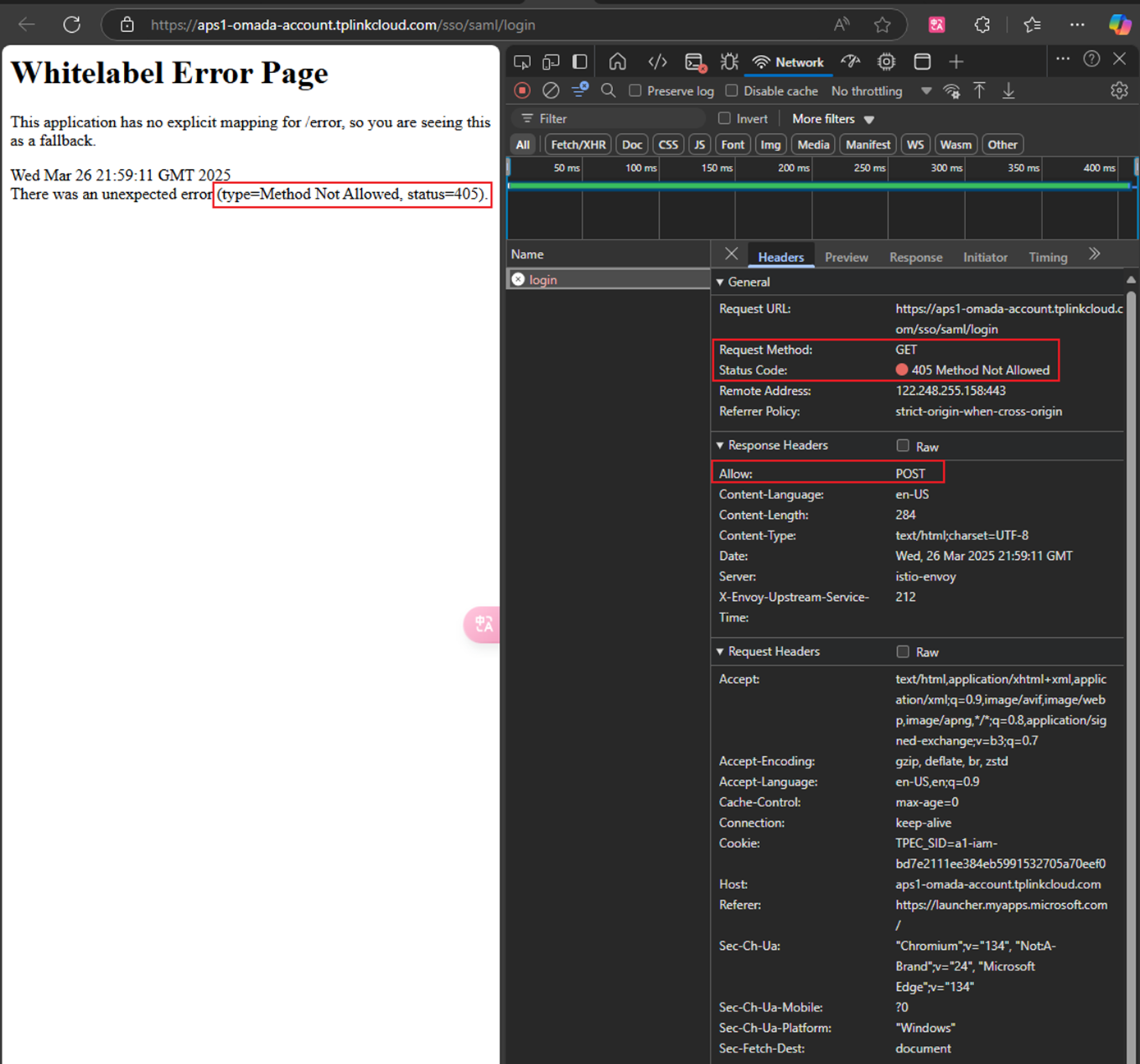
Re: From the dev tools, we can see that the Allow method for Response Headers is POST, but generally, the Request Method is GET. The technique is not matched.
Go back to your application's Basic SAML Configuration, choose Edit to configure the configuration, double-check the Identifier, Reply URL, and Relay State, and remember to clean the sign-on URL(Opential). Keep this blank.

2. What should I do if I meet the error code {"errorCode":-1001, "msg": "Invalid request parameters."} ?
Re: Go back to Part 2 Attributes & Claims to check whether you have set the username and usergroup_name and whether the value is correct.

3. What should I do if I meet the error code {"errorCode":-1, "msg": "Something went wrong. Please try again later or contact our technical support."} ?
Re: Go back to SAML Certificates; if you have more than one certificate, please delete the manually added ones.









