Contents
Configuring a Google LDAP Profile
Configuring VPN Rule Based on Google LDAP Authentication
Introduction
The Google LDAP feature in the Omada Gateway series works by functioning as an LDAP client. It is mainly used for two purposes:
- Portal authentication in standalone mode
- VPN authentication in standalone mode, including authentication for OpenVPN, L2TP VPN, and PPTP VPN. in controller mode, only OpenVPN supports this feature.
Requirements
- Omada Software/hardware Controller or Omada Central
- Omada Gateway
- Google LDAP server (Google’s paid LDAP Server)
Configuration
Configuring a Google LDAP Profile
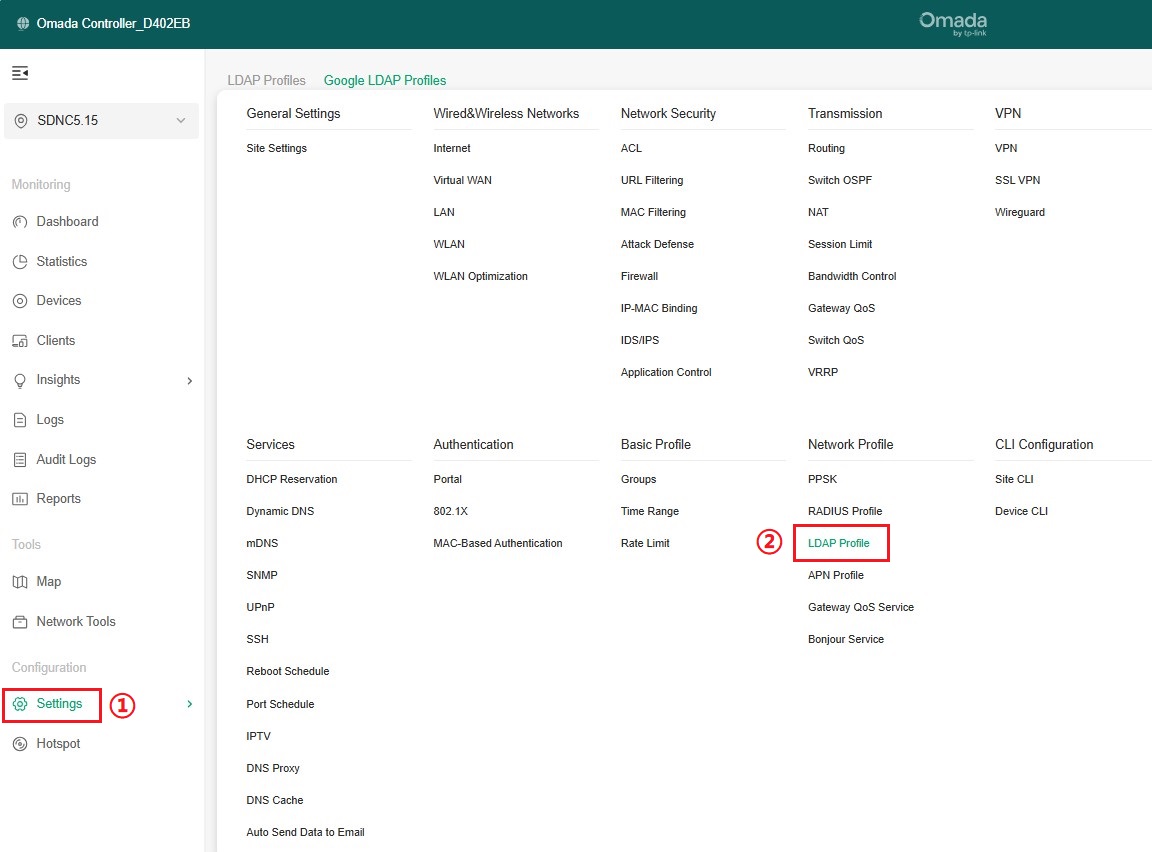
Step 1. In Controller Settings > Network Profile > LDAP profile, click Create New LDAP Profile.
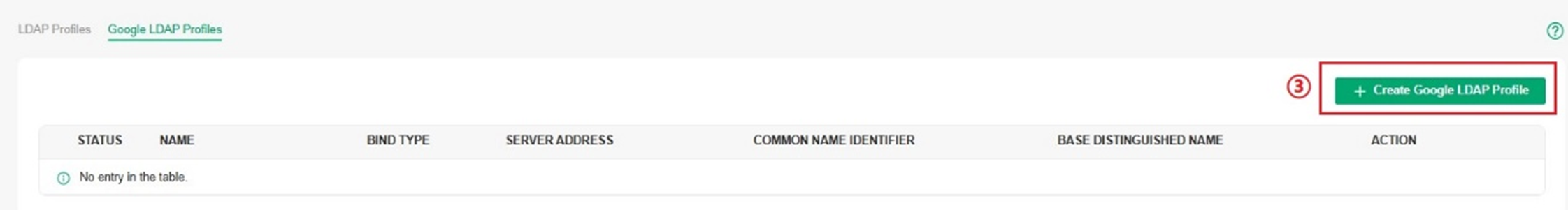
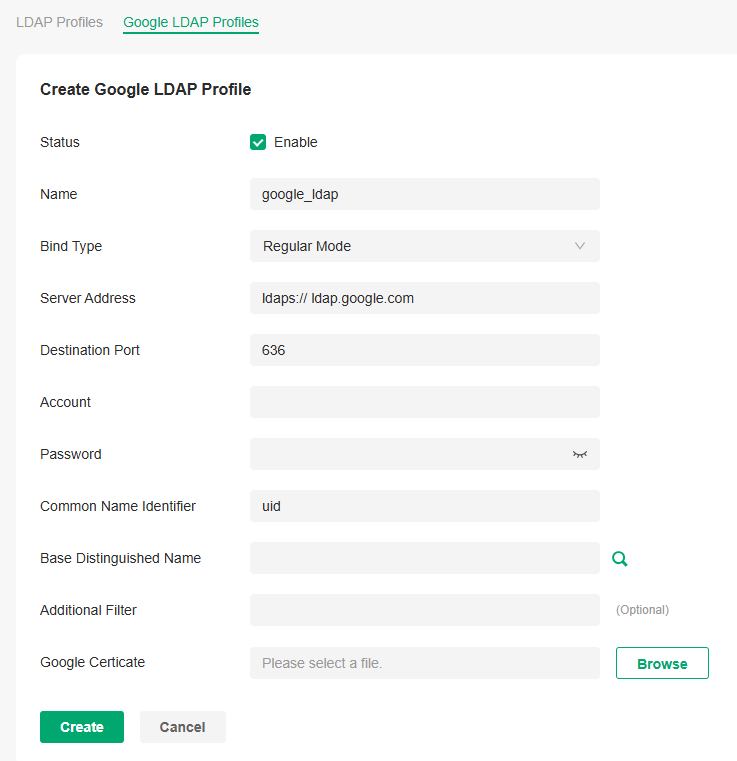
Step 2. Choose Bind Type, and configure the Profile accordingly.
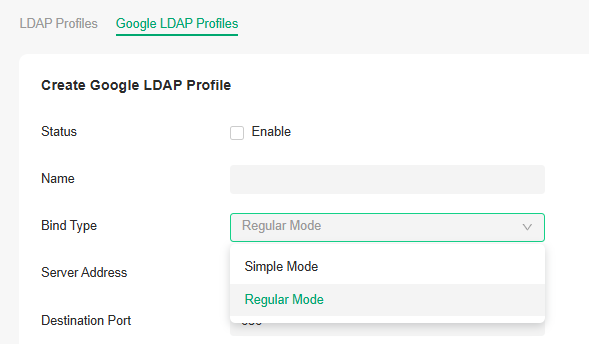
Two Bind Types are available:
Simple Mode: LDAP clients will send bind requests only without an administrator account and password or search query permission. This mode is mainly used for scenarios where authentication accounts belong to the same LDAP directory node.
Regular Mode: LDAP clients can send bind requests and search queries with an administrator account and password. This mode is used for scenarios where authentication accounts belong to the same or different LDAP directory nodes.
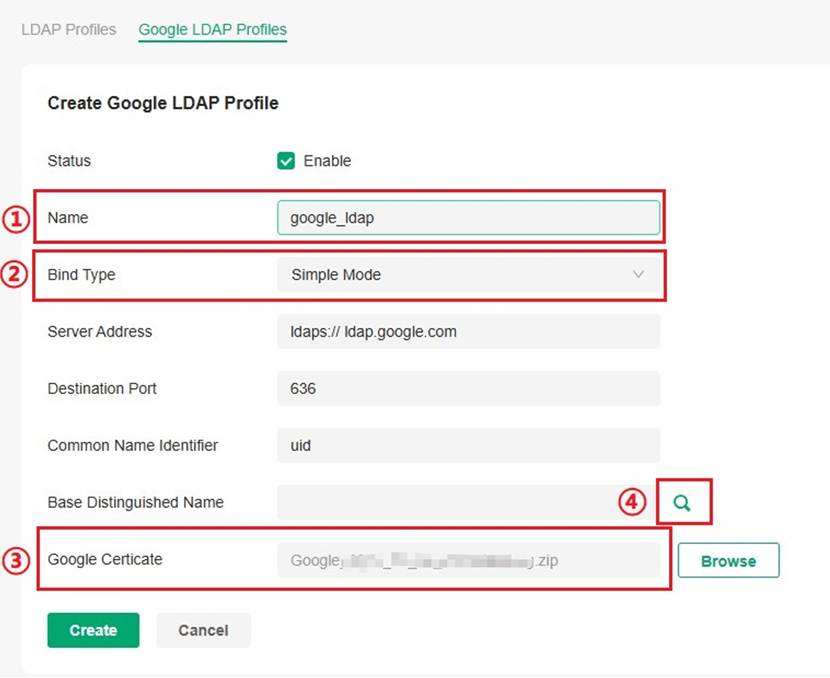
In Simple mode, you need to fill in the following parameters:
- Server Address: URL of the Google LDAP Server, fixed as ldap.google.com.
- Destination Port: The port ID of the LDAP server, set to 636 by default.
- Common Name Identifier: Usually uid, must match the user configuration on the Google LDAP Server
- Base Distinguished Name: The upper directory node in the LDAP Server where the users to be authenticated reside. You can click the search button on the right to view the directory structure and choose any node.
- Google Certificate: The Google LDAP server automatically generates a certificate.
Certificate download path:
- Sign in to your Google Admin console.
- Go to Apps > LDAP.
- Select a client.
- Click the Authentication card.
- Click GENERATE NEW CERTIFICATES.
- Download the certificate from the Certificates window.
- Upload the .zip file to the Google Certificate field.
In Regular mode, the following additional parameters are supported:
- Account: Credentials for the Google LDAP Server (unique to Regular mode)
- Password: Credentials for the Google LDAP Server (unique to Regular mode)
How to obtain Account/Password:
- Sign in to your Google Admin console.
- Go to Apps > LDAP.
- Select a client.
- Click the Authentication card.
- Click GENERATE NEW CREDENTIALS. You can then view the password in the Access credentials window.
- Additional Filter: (Regular mode only) — An extra filter; when filled in, an account must match the filter value to pass authentication.
Configuring VPN Rule Based on Google LDAP Authentication
Step 1. Go to the Controller management page: Settings -> VPN -> VPN.
Click the Create New VPN Policy button to enter the configuration page.
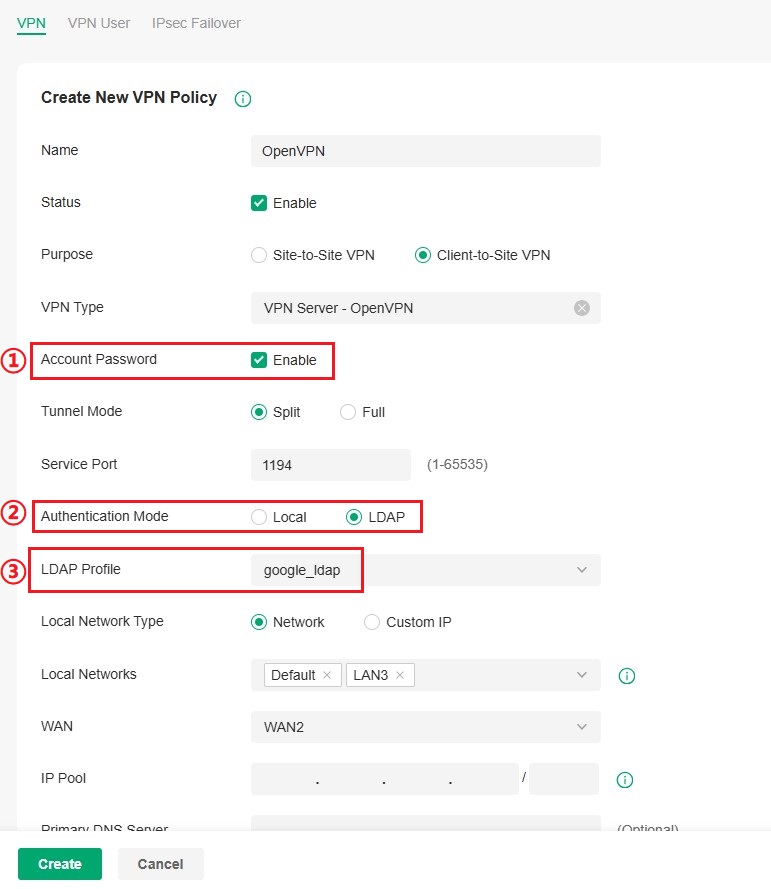
For OpenVPN based on Google LDAP authentication, select Client-to-Site VPN > VPN Server > OpenVPN.
Enable Account Password mode, select the previously created Google LDAP Profile and configure other parameters according to the VPN configuration guide.
Conclusion
This article introduced the steps for configuring a Google LDAP Profile on Omada Gateway series devices and applying it to VPN authentication.
Get to know more details of each function and configuration please go to Download Center to download the manual of your product.
QA
Q1. Why can't I connect to the LDAP server when configuring the LDAP Profile?
A1. Please ensure that your LDAP server parameters are configured correctly. You can verify them using a general LDAP client tool with the same settings.








